The Summary of Securing Switch Access PDF is a technical document that provides an overview of securing access to network switches. The document highlights the importance of securing switch access to prevent unauthorized access and protect the network from security threats.
It describes the different types of switch access, including console access, Telnet access, SSH access, and web access. The PDF also covers various security measures that can be implemented to secure switch access, such as strong passwords, access control lists, and port security.
The document concludes by discussing the benefits of securing switch access, including improved security, increased network availability, and reduced risk of security breaches.
Securing Switch Notes PDF
the Summary of Securing Switch Access PDF is a useful resource for network administrators and engineers who are looking to implement security measures to protect their network switches from security threats. Consisting Of 43 pages, in a simple style.


Securing Switch Notes Content
- Overview of Switch Security Concerns
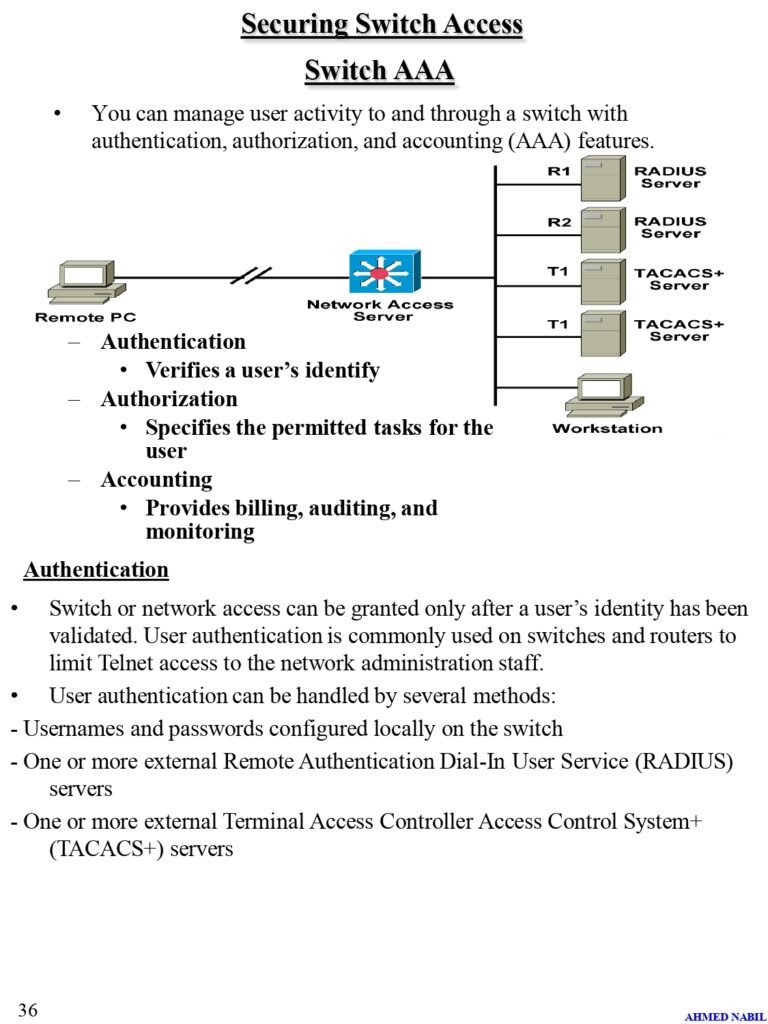
- Switch AAA
- Authentication
- Authorization
- Accounting
- Port-Based Authentication (802.1x)
- Switch Attack Categories
- Port Security
- DHCP Snooping
- VLAN best Practice + 802.1x
- BPDU Guard & Root guard
- Attacks on switch devices
- MAC layer attacks (CAM table overflow, Media Access Control (MAC) address spoofing )
- Spoof attacks (switch spoofing, ARP Spoofing & DHCP Spoofing) DHCP starvation
- VLAN attacks (VLAN hopping )
- Spanning-Tree Protocol (STP) manipulation
- VLAN Access Lists (VACL)
- MAC Access-Lists
- Private VLANs
Prepared By: –
Eng Ahmed Nabil
Notes Format: –
To Download PDF: –
For other Network Notes PDF From here
